
The promise of a new industrial revolution powered by Generative AI has ignited a global economic contest, yet for years, understanding Europe's actual position in this race has been an exercise in navigating speculation and fragmented anecdotes. While debates have raged about the technology's

The very foundation of cybersecurity strategy is undergoing a significant transformation, shifting away from the rigid frameworks of compliance checklists and toward a more dynamic, intelligence-driven approach focused intently on the adversary. This evolution, known as Threat-Led Defense,
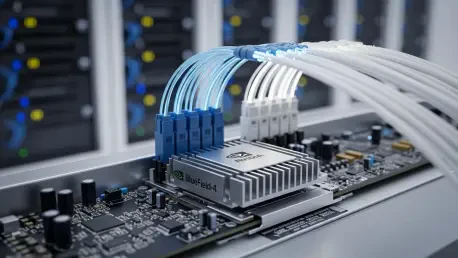
The relentless escalation of artificial intelligence workloads, pushing the boundaries of what trillion-parameter models and high-volume inference processing can achieve, has placed an unprecedented strain on the foundational architecture of modern data centers. As these complex computations become

A single point of failure within a core banking system upgrade can instantaneously freeze millions of transactions, creating a ripple effect of financial and reputational damage that can take years to repair. In today's interconnected business landscape, the line between an important project and a

In the uniquely fraught digital landscape of modern healthcare, a dangerous disconnect often exists between the appearance of security and its reality, where organizations that successfully pass regulatory audits still fall victim to devastating breaches. The prevailing "check-the-box" compliance

Navigating the landscape of do-it-yourself home security systems often leads consumers to a crossroads defined by two dominant industry leaders, Ring and Nest. Both platforms have earned their reputations by offering robust, user-friendly solutions that empower homeowners to take control of their